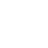Amazon released AWS WAF (Amazon Web Services Web Application Firewall) at AWS re Invent in 2015, Later, the introduction of managed rules in 2017 made it more popular.
Background
WAF (Web Application Firewall) protects your AWS Powered Web Applications from the common web exploits such as SQL Injection, cross-site scripting, file inclusion vulnerability, and security misconfigurations (attempt to gain unauthorized access or knowledge of the system and access default accounts, unused pages, unprotected files, and directories, etc.)
WAF provides us access control lists (ACLs), rules, and conditions that define acceptable or unacceptable requests or IP addresses. You can selectively allow or deny access to specific parts of your web application and you can also guard against various SQL injection attacks & XSS.
You can use WAF by attaching it to API Gateway, Cloudfront, Application Load Balancer (ALB)
You can use the following criteria to allow or block requests:
- Source/Origin IP address
- Source/Origin Country
- String match or regular expression matching in a request
- Size of the request
- Detection of malicious SQL code or scripting
Based on the criteria ACL can be used to block or allow web requests like the following:
- XSS, which enables attackers to inject client-side scripts into web pages viewed by other users.
- Origin IP Address or Range.
- Origin Country or geo-location.
- Length of particular parts of the request, for ex: query string
- SQL injection. Attackers embed malicious SQL code to extract data from the database.
- Part of any request, like, values that appear in the User-Agent, x-forwarded-for headers or text in query strings. You can use regex for identifying these strings.
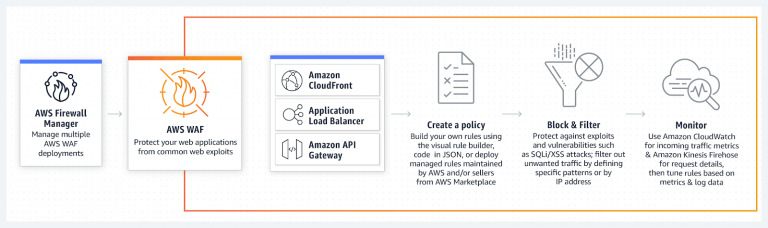
- Blacklist: IP addresses that you want to block.
- Whitelist: IP addresses that you want to allow.
SQL Injection (C) and XSS (D): The solution has two native AWS WAF rules that are designed to protect against malicious SQL injection or cross-site scripting (XSS) patterns in the query-string, URI or body of a request.
HTTP flood (E): This rule protects against attacks that exploit seemingly legitimate GET or POST requests to a server from a particular IP address, such as a web-layer DDoS (Distributed Denial of Service) attack.
Scanners and Probes (F): This component parses application access logs scans for unwanted behavior, such as the unwanted amounts of errors generated from a source. It identifies the suspicious source IP addresses & blocks them.
IP Reputation Lists (G): This component checks & blocks new ranges of IP addresses, with the help of IP Lists Parser AWS Lambda function for regularly checking third-party IP reputation lists and block them.
Bad Bots (H): This component relies on a honeypot URL, It is a security mechanism intended to lure and deflect an attempted attack.
But Cloudwatch Alarms doesn’t give the detailed monitoring & alerts on the 10-sec granularity for the blocked requests. As the alarm switch from Insufficient to Ok & vice versa, and state switching takes around 2-3 mins, which can miss the request being blocked during that interval.
Kinesis Data Firehose stores all logs in the S3 bucket, logs help us identifying why certain rules triggered & why certain rules blocked with our specific ALC rules.
Kinesis Delivery Stream is set on a buffer size of 5 MB and a buffer of 60 sec.
AWS CloudTrail Logs: CloudTrail provides a log of actions taken by a user, role, or an AWS service in AWS WAF. Using the information collected by CloudTrail, you can determine the requestor to AWS WAF, the origin IP address, time of the request, and additional details.
Further, automation of WAF can be done with managed & custom Web ACL’s, Rules with CloudFormation Template. It can be integrated with any automation toolchain that you may already be using. WAF can be implemented in your QA environment where the team can perform intensive penetration testing. Each team’s test cases can be run against the WAF Enabled Environment.
Thus, WAF is not just a reactive measure to implement security, it can also serve as a proactive measure to implement security through DevSecOps, which can be used in conjunction with CI/CD. With solid monitoring and logging integration, WAF can be a security center for your applications.